Note: Limera1n supports all 4th Generation iDevices, as well as the iPod Touch 3G and iPad 3.2.2+. I can confirm that this works on the 3GS without problem and the so-called lag is not noticeable to the untrained eye. There are no announced plans to support earlier iDevices as of this posting.
Here's the Greenpois0n step by step for you guys, screenshots provided by redmondpie.com, enjoy!
Be ready to move quickly, some of these steps will pass you by if you aren't ready for them. It is okay if you mess up a few times, forcing a hard reboot will allow you to start the process over again (to do this simply press and hold both the sleep button and home button until the device shuts off completely, then press the sleep button to power on, and restart the process). This works, and does not delete your stuff, I am living proof.
Step 1: Download Greenpois0n from here: http://www.greenpois0n.com
Step 2: Connect your iDevice to your computer via USB, power it off (shut down) and click on "Prepare to Jailbreak (DFU)"
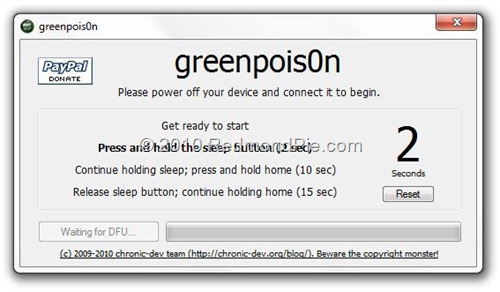
Step 3: Following the on-screen instrcutions:
- Press and hold the sleep button for 2 seconds
- Continue holding sleep; press and hold home for 10 seconds.
- Release sleep button; continue holding home for 15 seconds.
- Step 4: Your device is now ready for jailbreak. WHILE HOLDING ONTO THE HOME BUTTON Click on “Jailbreak” to inject the exploit. IMPORTANT: DO NOT LET GO OF THE HOME BUTTON AT THIS POINT
- Step 5: Your iPhone, iPad or iPod touch should now be successfully jailbroken on iOS 4.1 !
- DO NOT LET GO OF THE HOME BUTTON YET doing so will cause the process to fail and you will need to hard reset and start over
- Once you see the above screen, with the "Quit" button and "Jailbreak Complete!" shown, you can let go of the home button
- Step 6: Once your device reboots, make sure you are connected to the Internet and start “Loader” found on the homescreen (look on your last screen if you have multiple screens) and install Cydia (only thing in there). Note: "Loader" may appear to be whited out on your home screen, this is okay, continue as noted here to install Cydia.
Once Cydia is installed it will ask you if you want to remove loader, select continue and after restart go into Cydia. Make sure you select "Complete Update" when prompted in Cydia so everything works right.
This is it! You are done!
You will see what looks like a bunch of lines of code flash on your screen, pause for a few moments, and then your device will come up to your lock screen. This happens immediately following the jailbreak process and is normal.
Once you get Cydia installed, after the initial "Complete Update," there will be a lot of updates it requires, make sure you keep going back into the "Changes" section of Cydia so you get all the updates.
For you Rock users, Cydia and Rock are now one. Everything is done through Cydia. According to their own FAQ's, you simply need to download/purchase something from the Cydia store, create a Cydia account and your Rock licenses should transfer. Don't hold me to that, I have yet to see it work right on any device. The backup feature from Rock is not integrated with Cydia...yet...they say it is in the works.
Unlock for iOS 4.1 (Old Baseband) There is currently no way to unlock your iPhone on the latest 05.14.02 / 2.10.04 basebands. If you have managed to preserve your baseband while upgrading to iOS 4.1 using TinyUmbrella, you can use the existing version of Ultrasn0w to unlock your iPhone on iOS 4.1. Step by step instructions for unlocking can be found here.
Feel free to post questions here and I will respond in kind.
Enjoy!
-Geek
UPDATE 08-NOV-2010: I have been using this JB on my iPod Touch 2G since its release and it functions, however, because of the inferior hardware of my second generation device, I am limited as to which programs & themes will run correctly, if at all. As such, when jailbreaking an older device (earlier than 3G, except for iPad) be wary of what you install in regards to themes and newer apps. The 1G & 2G devices simply do not have enough power, which is why multi tasking is disabled on them by default from Apple with iOS4. If you can, keep your 1G & 2G devices running iOS <4.0.1 and use http://jailbreakme.com to jailbreak the device, it will run much better. - Geek
UPDATE 06-JULY-2011: @Comex just released Jailbreakme. 3.0 for all iOS devices <4.3.3...go to http://jailbreakme.com now to JB your iOS device for life!